The Mitigation of Security Litigation Premises Liability Lawsuits
 Most security driven litigation results from claims of inadequate security. This occurs most frequently when a guest or invitee allegedly becomes victimized by the criminal acts of a third party while on the property of the enterprise being sued. There are occasions that an invitee alleges victimization by an employee or contractor of the property owner, sometimes constituting an intentional tort. In most cases, the claims of victimization include some level of personal injury, either physical and/or emotional or both.
Most security driven litigation results from claims of inadequate security. This occurs most frequently when a guest or invitee allegedly becomes victimized by the criminal acts of a third party while on the property of the enterprise being sued. There are occasions that an invitee alleges victimization by an employee or contractor of the property owner, sometimes constituting an intentional tort. In most cases, the claims of victimization include some level of personal injury, either physical and/or emotional or both.
SMSI Inc. is a security consulting firm. As security consultants, we are frequently called upon to render opinions regarding the credibility of such claims. We are retained by law firms who may be representing the plaintiffs or defendants in these matters. We have been providing these Expert Witness services for over 30 years, covering most states and part of the Caribbean. We are also security consultants. As security consultants, part of our mission is to try to reasonably reduce the probability that our clients will be exposed to the premises liability claim of inadequate security. When it comes to security derived litigation, we have found the cost of reaction, is several times greater than the cost of being proactive. In fact having a reasonably secure hospital, hotel, shopping mall, high-rise building or educational institution, et al., is simply good business.
Those enterprises that have effective security programs and are generally perceived as being safe, are much more successful that those enterprises that are perceived as being dangerous. One of the points we are trying to make here is that perception matters. In fact, we recently spoke with a security forum, sponsored by Campus Security Magazine on the topic of The Psychology of Security Programs; The Essence of CPTED. (CPTED: Crime Prevention Through Environmental Design).
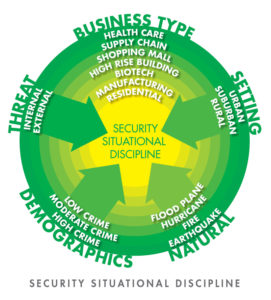 Security is very much a situational discipline, meaning that one size does not fit all. This graphic depicts the various factors that impact the components of most security programs. Additionally, the external environment is dealt with differentially from one industry to another. For example, hospitals, from a liability perspective, have one of the highest standards of care, where a manufacturer may have a substantially lower standard of care from a liability perspective, but may have a very high standard of care for the protection of data, products and employees. Supply chain facilities that are unable to keep products safe, may also be exposed to security driven litigation.
Security is very much a situational discipline, meaning that one size does not fit all. This graphic depicts the various factors that impact the components of most security programs. Additionally, the external environment is dealt with differentially from one industry to another. For example, hospitals, from a liability perspective, have one of the highest standards of care, where a manufacturer may have a substantially lower standard of care from a liability perspective, but may have a very high standard of care for the protection of data, products and employees. Supply chain facilities that are unable to keep products safe, may also be exposed to security driven litigation.
The good news is that the security programs of today are much more cost efficient than they were 15 years ago. This means there is less reliance on manpower and the associated costs. In the last few years there have be tremendous advancements in access management, smart video and architectural design (CPTED), even to the built environment. There is much more partnering between local Police jurisdictions, and private security operations. We are seeing this partnering manifest itself most recently in the response and mitigation of active shooter events affecting schools, shopping malls and hospitals.
In order to mitigate against litigation driven by the assertion of inadequate security, one of the best first steps is to commission a comprehensive security review in-order to establish a foundational predicate for all that follows.
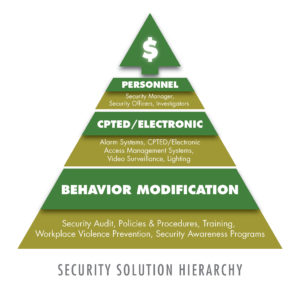 The Security Solution Hierarchy, depicted here illustrates that there is a logical construct to building an effective and cost efficient security program. You will note that the less costly remedies are applied first, with the more costly remedies applied last, and only if needed.
The Security Solution Hierarchy, depicted here illustrates that there is a logical construct to building an effective and cost efficient security program. You will note that the less costly remedies are applied first, with the more costly remedies applied last, and only if needed.
One should not conduct a security assessment for the sole purpose of reducing liability. Obviously, that is always a goal, but beyond that, it is simply good business, and often results in a more positive employee morale. Employees feel better when they have a safe workplace to come to every day. Additionally, the most effective security programs engage their employees to become part of the solution, as opposed to being part of the problem. Happy employees mean increased productivity.
Finally, once an effective security program has been established, the goal is to keep that security program contemporary. Remember, the security threat environment is dynamic.
There are continual nuance changes in the threat environment, and those changes differ for schools, hospitals, malls, HOAs, hotels and supply chain facilities, and they are not synchronous.
The best hedge against obsolesce is data, both external and internal. The local Crime Environment is well defined by the Products such as the CAP Index (www.capindex.com). There is also the availability of crime data from local law enforcement jurisdictions. The CAP Index will give local law enforcement data context.
Internal data is also important. If your organization is still using a handwritten report format, you are probably in the Dark Ages. More important than the documentation of Daily Activities and Security Incidents is the ability to retrieve that data and to subject it to statistical analysis.
Luckily there are very good options available for the tracking of both Daily Activity Logs and Incident Reports. These cloud based systems are easy to use and they provide a level of sophisticated Trend Analysis that was nearly impossible with hand written reports. These reporting systems have a portability component that allow security officers to enter and/or receive data on a portable device.
One of the best low cost solutions is ReportExec (www.reportexec.com) from Competitive Edge. Over the years, we have found that security managers who know how to speak the language of the C-Suite, are much more likely to get their budgets approved than those that do not back up their Proposal with projective statistics.
Summary
We started this presentation by promoting the notion that security, which is a proactive, situational discipline, when properly applied, can reduce the probability of security driven litigation. We also made the point that the mitigation of litigation exposure should not be the only driver of your security program, but liability mitigation should be one of the products of an effective and comprehensive security program along with many other quantifiable benefits.
We believe the best first step is a comprehensive security assessment, and that is what we do. By some measure our services in the realm of our security litigation support, as security experts, is similar to the services we provide proactively. However, the former is usually more cost effective than the latter.
William H. Nesbitt, CPP
President
Security Management Service International
Phone: 805-499-3800; Email: bill@smsiinc.com

