SECURITY MANAGEMENT SUPPORT (An Alternative Security Management Model)
As posted on LinkedIn Pulse 9/7/16
It was not that long ago that the dominant item on many security department budgets, was payroll burden. In today’s world that may, or may not be the case. Thanks to the advancements made in cost-efficient security technology, the demand for payroll burden has generally been reduced, to greater or lesser degrees, depending on the industry being affected. Technology has not completely eliminated the use of security personnel, but because to technology, fewer security officers have become more effective. This supports the notion of doing more with less.
Consistent with this cost-effective genre, the notion of security management support has become a viable methodology for many security existing security programs, as well as to future security programs. To be optimal, all security programs should be cohesive, and integrated with unity of purpose. With effective synergy one will assure that the whole will be greater than the sum of the parts. It is now possible to do more with less. SMS solutions have the capability to make available a team of diversified security expertise to ensure that security remedies are need driven as well as industry specific.
The intended goals of a Security Management Support Program are to:
- Ensure that every security program is need driven and contemporary
- Ensure that each security program is producing the measurable results
- Ensure that each security program is leveraging cost efficiency
- Ensure that each security program remains contemporary going forward by adjusting to dynamic changes in the ambient threat environment
SMS Rationale
Those who purchase security services and security technology are often at a disadvantage, in that the vendor knows more about what he/she is promoting, than the customer knows about what he/she is signing up for. All security decisions should be driven by specifically identified needs.
Security professionals that offer SMS services are generally not engaged in the provision of uniformed security officers, access control systems, security alarm systems, and or video surveillance systems, these security professionals are able to make recommendations predicated on need and without bias or favor. To do less, may present a conflict of interest.
Contemporary Security Management
Effective and comprehensive security programs should not be the sole domain of large multi-national organizations. In fact, small businesses have even less capacity to absorb preventable losses. When any enterprise suffers losses that are attributed inadequate or ineffectual security, the cost of those losses, both direct and indirect, will often exceed the cost of prevention. Those losses may include the misappropriation of inventories, cash, information and/or personal injury of employee and invitees.
Those industries that are open to the public, have legitimate premises liability concerns. This includes the mitigation of premises liability lawsuits. Affected verticals include shopping malls, hospitals, the lodging industry and sports and entertainment venues.
As most business entities are well aware, it is not infrequent that the indirect costs, of any category of losses, will often exceed the direct cost of loss. Most security litigation cases assert that the security program was inadequate because it did not reasonably prevent the alleged security beach. Inadequate security claims may be related to perimeter, the lack of security personnel, perimeter control and lighting. To a lesser degree, intentional tort cases stem from claims such as the alleged use of excessive force, false arrest, and or, false imprisonment. The question always comes down to the question as to whether the security program was adequate, give the ambient threat environment.
It is important to remember that security should be a proactive discipline. As previously stated, on the positive side of the ledger, security technology continues to become more cost efficient, and more effective. For example, consider the advancement of video surveillance systems. These systems have improved exponentially over the past several years, while at the same time, becoming less costly, much more effective, while at the same time, helping to reduce dependence on security FTEs.
Additionally, behavior modification techniques have become the glue that holds security programs together, making them more effective. The application of CPTED (Crime Prevention Through Environmental Design) is just another example of cost efficiency, without sacrificing the ability to reasonably mitigate security breaches.
Those who are making the budget impacting security decisions should not be limited by inexperience, nor should they be encumbered by a knowledge and experience deficiency when committing limited assets to the purchase of security services and security technology.
There are a number of potential security remedies that have very little budgetary impact, such as the application of behavior modification strategies, such as CPTED being just one example.
The primary driver of security decisions must be data. Computer Based Security Management Support products are a must. Security management systems will ensure that each security program is responsive to an ambient, and dynamic, external and internal threat environment. These systems will help to ensure that minor security beaches do not morph into an out of control trend. Mitigating security beaches at the incipient stage is more cost efficient than dealing with a well-entrenched pattern.
Not every enterprise requires a full-time Board Certified Protection Professional (CPP). However, most enterprises would benefit from this expertise from time to time. This is the purview of those who offer Security Management Support (SMS) programs. Those who offer these services will normally bring a problem solving team of diverse security experts to the table. Typically, SMS programs are able to offer supportive services in dealing a wide range of security vendors by ensuring your security program is need driven, and optimally cost-efficient. As you will note: the Security Solution Hierarchy (SSH) below is a progressive model for most cost efficient security programs. Unlike previous iterations, this SSH model presents each level as offset. The purpose of the offset design is to acknowledge, predicated on a needs assessment, that all four levels may not be justified, given the ambient threat environment. For example, CPTED and Behavior Modification, coupled with a modest locking system, may be sufficient for some clients.
We believe that those security professionals who are engaged in security management support, should also bring objectivity to the table. This assumes the absence of any conflict of interests, such as the provision of guard services, alarm systems, access controls systems and/or video surveillance technology.
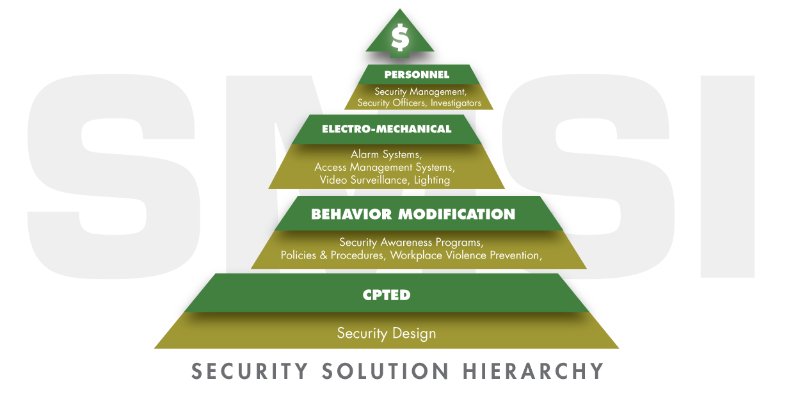
Finally, we offer the previously mentioned model, the Security Solution Hierarchy (SSH). The Security Solution Hierarchy merely provides a prioritization road-map as a guide to an effective and cost efficient security plan by ensuring that less costly remedies precede more costly remedies. In many cases, depending on the ambient threat environment, the less costly remedies may be sufficient. When applying the SSH model, from the bottom up, it is not always necessary to apply all four levels. For example, the application of CPTED and Behavior Modification may be sufficient, especially when the ambient crime rate is very low. The four levels of the Security Solution Hierarchy are intended to be a model for the rank-ordering of potential security solutions, thus assuring that the whole is greater than the sum of the parts.
Security Management Support is not intended to be a replacement for traditional security management models. SMS is intended to provide an alternative to those enterprises that may not have the budgetary justification for a full-time credentialed security manager. However, most all clients would benefit from the expertise of a well-qualified security management team, as needed, especially when considering the application of emerging cost-beneficial security technologies that may lower the dependency of security FTEs. Finally, when seeking security management support, the provider of these services, should be independent, and should not be tied a particular security product and/or guard service, in order to assure objectivity.
The SMS offering will bring a team of diverse and well qualified, credentialed security and loss prevention expertise to your organization, without the attendant payroll burden. This team will ensure fair and competitive pricing from a wide and diverse group of security vendors.
What industries might benefit from SMS? (Hospitals & Healthcare Facilities, Shopping Malls, Hotels, Small to Medium Manufacturing Plants, Schools, Office Buildings & Residential Complexes)
Results: A cost efficient, yet improved & synergistic security program.
William Nesbitt, CPP, Certified CPTED Practitioner; President SMSI Inc.
Ron Lander, CPP, CMAS (Certified Master Anti-terrorism Professional),
PSM Physical Security Manager Certification; Vice President SMSI Inc.
Contact Information: www.smsiinc.com; bill@smsiinc.com
Phone: 805-499-3800
