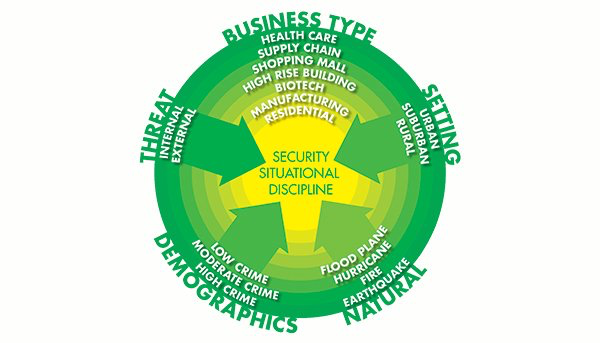
Security is a Situational Discipline The Language of the C-Suite
Security is a situational discipline. If you subscribe to this notion, then every security program is unique unto itself. For example, security programs that are industry specific, are consistent with other security programs, yet still unique within the confines of the industry being served. Hospital security programs are differentiated from mall security programs and/or school security programs. Additionally, within the healthcare vertical, no two hospitals are the same, nor should they be. In other words, within any vertical, there are unique characteristics among security programs, in part determined by the uniqueness of the threat environment (both internal & external).
These means that the security programs of Schools, Hospitals, Hotels and Manufacturing operations are differentiated between, and within each vertical. One of the differentiating variables is the risk factors generated by the ambient threat environment, both internal and external. Most security programs have similar objective, but the means for meeting those objective are diverse.
However, site specific data is required, first to design the security program, and second, to maintain and effectiveness security programs. The driving force for both is hard data, including crime risk information. The second reality is that the threat environment is subject to change, which means security programs must flex and adapt on a regular basis.
Therefore, managing a security department without using a security management system such as Report Exec is like going into a fight with one hand tied behind your back. Report Exec, based in Franklin, Wisconsin and PPM 2000, based in Edmonton, Alberta have developed security management tools that speak the language of the C-Suite. The principal language of the C-Suite is “quantifiable data,” that expresses return on investment that, in turn, justifies security budgets.
However, the ability to communicate with the C-Suite is just one of the benefits derived from systems like Report Exec. This tool provides security managers with the information needed to administer complex security programs at the local level, as well as nationally, and even globally. This information also becomes a critical tool when circumstances demand specific security breach investigations, such as the determination of motive, means and opportunity.
For the most part, prior to computer-based systems, daily activity reports (DARs) and incident reports (IRs) were recorded by hand and the veracity of theses reports was reliant on the capabilities of each security officer. These reports would eventually find their way into a binder and/or a file cabinet. This arcane methodology had two major inherent weaknesses: (1.) The quality of these reports was dependent on the skill-set of the recording security officer & (2.) the data was not categorized, and most importantly, it was not easily retrievable. Every security program must occasionally adjust to variations in the threat environment. With systems such as Report Exec, sophisticated trend analysis is only mouse click away.
In the past informed guesswork and the intuitiveness of security professionals provided the backbone for the development of most security programs. Sometimes these decisions were spot-on and other times, not so much. Now-a-days decisions regarding video surveillance, the allocation security personnel, including sophisticated trend analysis, are readily available.
Over my 35+ year career as a security professional it, it has become increasingly clear to me that security managers must be able speak the language of the C-Suite, not the other way around. This is one of the reasons I attended the ASIS International sponsored security management program at the Wharton School.
Here is an example of the power of data: Several years ago, when security management systems were in their infancy, I knew a security manager who had a very early version of this technology. This manager required that his security officer should record every incident and every daily proactive activity they took in the course of each shift. One this manager was called into the CEO’s office. He was told to come back with a plan to cut his budget by 20%. He was asked to come back with a plan in one week. The security manger went back to his office and quickly produced a spreadsheet that cataloged every security officer’s proactive activity for the past three years; such escorting female employees to their cars, removing squatters from the property, closing and locking doors that were left ajar, etc.
He returned the office of the CEO in less than one hour and asked the question: “Which of these services do you want me to curtail?” The CEO smiled and said, “Get out of here.” The request to cut was withdrawn. This is the power of data.
Security management systems help to support relevancy of security design as well as quantify return on investment. These systems provide a tool to reduce risk and significantly reduce liability and claims of negligence. These systems also provide the means to conduct sophisticated investigations of, both internal and external breaches with pinpoint accuracy.
Today’s budgetary environment demands that the funding of security programs is fully accountable. This accountably is applicable to single locations as well as system wide.
Finally, in addition to the use of security management system, we believe an objective stem to stern security assessment should be undertaken every five years, or so. Periodically, one must establish a predicate for all decisions that follow. Additionally, because security technology is moving forward at warp speed, cost efficient solutions may be applicable going forward. All security programs should also incorporate CPTED design. Security management systems will provide the evidence for budget efficient decisions going forward.
Remember, no matter what the industry being is being serve; Security is always a Situational Discipline driven by a unique set of needs.
William H. Nesbitt, CPP (bill@smsiinc.com)
President of SMSI Inc.
Our LinkedIn Group:Security Source Online