THE OBJECTIVE: ENSURING THAT THE WHOLE IS GREATER THAN THE SUM OF THE PARTS
As posted on LinkedIn Pulse 10/24/16
Every security program should be need driven because security is very much a situational discipline. The individual components of each security program should be need driven as defined by the current ambient threat environment and the mission of the enterprise being protected. As we have stated in previous articles, the backbone of every security program is defined by the Security Solution Hierarchy (SSH).
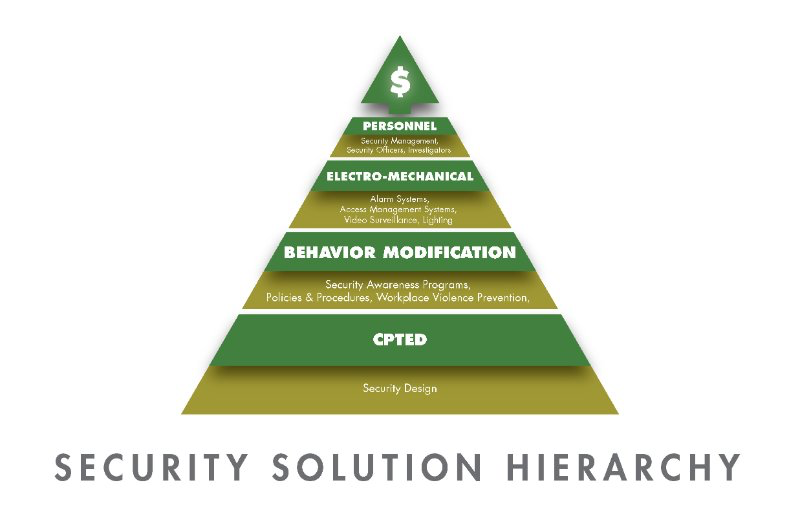
The security solution hierarchy helps to establish a construct of prioritization. The mission of every security program should be to create an environment where the various components of the security program (security officers, video surveillance systems, access control systems) and security strategies such as CPTED) are all synergistically addressing the mission ay hand. If the components of the security program are disparate and incongruent, any return of investment will likely be marginalized. For example, the potential benefits to be derived from access control systems may be diminished, to some degree, if they are applied in a vacuum. Every employee should have a role in helping to maintain the integrity of access control programs, as well as all electro/mechanical security strategies. This creates an effective multiplier effect for every security budget.
Video surveillance systems, if not properly monitored may well become a liability, in a premises liability lawsuit. Inadequately trained security personnel may potentially increase liability than would the absence of security officers. Inadequately trained security personnel is often manifested in matters such as excessive use of force, if they are not properly trained, and/or improperly posted.
You will note that the bottom of the SSH model begins with CPTED, with security personnel at the top. The purpose of the SSH strategy, is to encourage less costly remedies first, followed by reassessment, prior to moving up through the remaining three levels. As one moves up through the pyramid, there should be a consideration whether the next level is justified, given the ambient threat environment, both internal and external. Two or three levels may be sufficient in some cases. Ironically, the practices of many organizations, is to start a to top with security officers, and work downward, thereby assuring cost-inefficiency.
Security programs must always be situationally adaptive. This suggests that the starting point should be an objective comprehensive security risk assessment. It is also important to keep in mind that the precursors of criminal activity are motive, means and opportunity. Any security program that fails to identify and quantify these three preconditions, will more likely than not, come up short. Of the three preconditions, the primary focus of most security programs, is the reduction of opportunity. This challenge requires a combination of both physical deterrence and psychological (behavioral) deterrence.
The preconditions of motive, means and opportunity must also be considered within the context of a quantified threat environment. Among the plethora of choices of potential security measures available, cost effectiveness will surely become a major factor when considering all available options.
The desired end, with help to justify the means. The value being promoted here, is to ensure that every security program meets the goals of ensuring that TheWhole is Greater Than the Sum of The Parts. This is an achievable and measurable objective goal that will also result in measurable cost- efficiency. The Security Solution Hierarchy, not only provides a guideline for the sequencing of security remedies, it also implicitly reinforces the notion of a layered approach for effective security.
Security programs that are driven by the notion that the whole should always be greater than the sum of the parts, will likely be viewed favorably by the C-Suite. If this concept may seems simplistic, it is. However the devil is often in the details. This goal is achievable, and much more likely to be attained if it is before the fact.

In our work, as security consultants, it is not infrequent that we find a number of desperate security strategies that are isolated and completely lacking the linkage of synergy. Security programs, lacking synergy, when the goal does not consider that the whole is greater than the sum of the parts, will almost always come up short.
As one considers the application of security officers, video surveillance systems, access control systems and barrier systems, the interrelationship of each of these components, should also be taken into consideration. It is the interrelationship between various methodologies, that ensures that the whole will be greater than the sum of the parts.
Like many security concepts, the fundamental are simple. The execution may be more complex. Security program lacking employee and/or tenant involvement, are doomed to mediocrity. When was the last time you conducted a thorough objective security assessment?
William H. Nesbitt, CPP, Certified CPTED Practitioner
President Security Management Services International Inc. (Security Consultants & Litigation Support)
Phone: 805-499-3800; Email: bill@smsiinc.com
Member: ASIS International, IAHSS, ASHRM, SCHARM, ACHE, ICA
